Be yourself; Everyone else is already taken.
— Oscar Wilde.
This is the first post on my new blog. I’m just getting this new blog going, so stay tuned for more. Subscribe below to get notified when I post new updates.
Be yourself; Everyone else is already taken.
— Oscar Wilde.
This is the first post on my new blog. I’m just getting this new blog going, so stay tuned for more. Subscribe below to get notified when I post new updates.

Hi! I’m Syaza. I am student from University Tun Hussein Onn Malaysia (UTHM). I’ll share my resume, job letter, company profile and video resume. I also include some photos of activities that I join.
Click this link to view my video resume. https://youtu.be/-CB_2kETHZM



I joined Firefighter Institution as my extra-curricular activities at UTHM.





Hiking at Bukit Mor with Kelab Iqra’s members.





Kelab Iqra’ held Kem Muslim Produktif and it focused on leaderships skills.







“Gunung Ledang Mu Tunggu Aku Datang” program with Kelab Iqra’ society. We hike the Mount Ledang and having some funs challenging activities at Asahan Water Theme Park.





I participated as contingent representing Iklas Johor during Independent Day.





Doing my experiments with my classmates and lovely lecturer.

MULTIMEDIA CONCEPT & TOPICS
Multi is more than one. Medium is middle. Media is means for conveying information. Multimedia refers to various forms text, image, audio, video, graphics and animation in a variety of application environments.
Mass media is media in the press, newspaper,radio and TV contect. Transmission media is media in communication such as satellite, cables and networks. Storage media is media in computer storage such as floppy, CD, DVD, HD and USB. Interaction media is media in HCI context such as text, image, audio, video and CG.

CHAPTER 6 TELECOMMUNICATION (ETHICS, FILTERING AND PRIVACY)
In this chapter, I will write about the risk of telecommunication. A computer security risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information or processing capability. A cybercrime is an online or Internet – based illegal act. Some of the example are hackers, crackers, script kiddies, corporate spies, unethical employees, cyber extortionist and cyber terriorist. Computer security risks involve Internet and networks attacks is by virus attack. Unauthorized access and use are done by intercepting wireless communication. The example of hardware theft is stolen computer meanwhile illegal copying is an example for software theft and information theft is about stolen identity. Lastly, system failure is happens because of lightning strike. Ethics and society aware us that content filtering is the process of restricting access to certain material on the web.

CHAPTER 5 TELECOMMUNICATION (INTERNET, WORLD WIDE WEB & RESOURCE SHARING)
This chapter is about how a computer communicate with other computers. The World Wide Web (www) is a collection of document, image, video and sound files that can be linked and accessed over the Internet using a protocol called HTTP. HTTP Cookie is a small chunk of data generated by web server and stored in a text file on your computer’s hard disk. HTML is a set of specifications for creating documents that a browser can display as a web page. Uniform Resource Locator (URL) is a string of characters that points to a specific piece of information anywhere on this web. URL consist of the protocol (http, https, ftp), domain name or web server, the directory on the server and file within the directory. Two popular type of web search tools are search engine and subject directory. A search engine is helpful in locating items such as images, videos, audio, news, maps, people or businesses and blogs. Multimedia refers to any application that combines text with graphics, animation, audio, video and virtual reality. E-commerce is a business transaction that occurs over a network. Other than that, Instant Messaging (IM) is a real-time Internet communications service. VoIP is refer to Voice over IP which enables users to speak to other users over the Internet.
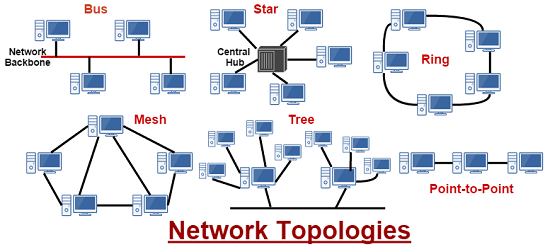
SUMMARY OF CHAPTER 4 (TELECOMMUNICATION – Communication & Network Concepts)
What are computer communication? It is a process in which two or more computers or devices transfer data, instructions, and information. The successful communication is needed to sending device, communication device, communication channel, communication device and receiving device. Some use of communication technology are Internet, Web, E – mail, Smart Television and video conferencing. Two types of communication are point – to – point and multipoint. As an example Smart Television could ve differentiate between interactive TV, Personalized TV and Internet TV. There are several types of networks such as Local Area Network (LAN), Home Area Network (HAN) and Personal Area Network (PAN), Wide Area Network (WAN) and Metropolitan Area Network (MAN). There are two type of networks structure which is client/server and peer to peer (P2P). Next, we have Intranet, Extranet and Virtual Private Network (VPN). Three commonly used network topologies is Bus Network, Ring Network and Star Network.

SUMMARY OF CHAPTER 3 (OPERATING SYSTEM)
Operating system is the most important thing in computer. Computer could not function without the operating system. What are the function of ab operating system? Some of the functions are to start the computer, provide a user interface, manage program, manage memory, schedule jobs and configure devices, establish an Internet connection, monitor performance, provide file management and other utilities, control a network and administer security. System software is programs that control operation of a computer. Next, Graphical User Interface (GUI) function to ensure that user interacts with menus and visual images such as icons and buttons. There are 3 types of operating system such as embedded, network and stand-alone. The latest stand-alone operating system is Windows 10. The example embedded operating system is Google Android, IOS and Symbian OS. The function of Utility program is about file manager, backup and restore, file compression and device drivers.

CHAPTER 2 ( COMPUTER HARDWARE COMPONENTS )
In previous post I write about the information technology but now I will write about computer hardware components. So, what is system unit? System unit is a case that contains electronic components of the computer used to process data. There are some important major components in system unit such as processor, memory, adapter cards, ports, drive bays and power supply. The main circuit board in system unit is called as motherboard. Central Processing Unit (CPU) functions to connect data into information. It is a must to have Arithmetic/Logic Unit (ALU) in every computer to perform arithmetic operations and logical operations such as addition, subtraction, evaluates condition and make comparisons. There are four operation of the CPU make up a machine cycle. Step 1 is Fetch : obtain program instruction and data from memory. Step 2 is Decode : translate instruction into commands. Step 3 is Execute : carry out command. Step 4 is Store : write result to memory. Computer have two types of storage which is Primary and Secondary. Ports connects external devices to system unit meanwhile connectors joins cable to peripheral. What is a bus? Bus is a channel that allows devices inside computer to communicate with each other. Lastly, bay is an open area inside system unit used to install addition equipment and typically hold disk drives.
SUMMARY OF CHAPTER 1 ( INTRODUCTION TO IT )
In this chapter we will learn about the definition of IT ( Information Technology ). IT is very common thing among nowadays generation. This chapter also cover about world of computer which is about the computer literacy, the definition about computer and computer’s components. Computer information processing cycle is include input, process, output and communication. The component of a computer must have input devices, system unit, output devices, storage and communication device. There are some feature that make computer so powerful such as the storage, reliability and consistence, speed, accuracy and communication. Computer consist of two type of computer software which is system software and application software. The programmer is someone who develops application or system software. The usage of a computer could be more advance with networks and Internet. Network is a collection of computers and devices connected together while Internet is worldwide collection of networks that connects millions of computers. There are some examples of computer applications in society such as education, finance and industry.
This is an example post, originally published as part of Blogging University. Enroll in one of our ten programs, and start your blog right.
You’re going to publish a post today. Don’t worry about how your blog looks. Don’t worry if you haven’t given it a name yet, or you’re feeling overwhelmed. Just click the “New Post” button, and tell us why you’re here.
Why do this?
The post can be short or long, a personal intro to your life or a bloggy mission statement, a manifesto for the future or a simple outline of your the types of things you hope to publish.
To help you get started, here are a few questions:
You’re not locked into any of this; one of the wonderful things about blogs is how they constantly evolve as we learn, grow, and interact with one another — but it’s good to know where and why you started, and articulating your goals may just give you a few other post ideas.
Can’t think how to get started? Just write the first thing that pops into your head. Anne Lamott, author of a book on writing we love, says that you need to give yourself permission to write a “crappy first draft”. Anne makes a great point — just start writing, and worry about editing it later.
When you’re ready to publish, give your post three to five tags that describe your blog’s focus — writing, photography, fiction, parenting, food, cars, movies, sports, whatever. These tags will help others who care about your topics find you in the Reader. Make sure one of the tags is “zerotohero,” so other new bloggers can find you, too.